Military Encryption Software - Sharing lockers with other NordLocker users, including free edition users, is a breeze. You simply send the locker to the recipient's email address and NordLocker will take care of encrypting the sent version with the recipient's key.
If the snoop or spy doesn't even know you've hidden sensitive files, there's no way to find them. Even if you don't need this level of protection, Steganos Safe offers more versatility in encrypted storage than others.
Military Encryption Software
 Source: m.media-amazon.com
Source: m.media-amazon.com
Back in the day, if you wanted to keep a document private, you could use a cipher to encrypt it and burn the original. Or you can lock it in a safe. These options correspond to two main approaches to encryption services.
Who It’s For
An encryption algorithm is like a black box. Put a document, photo or other file on it and you get something that looks like crap. Put the nonsense back in the box with the correct password and get the real thing.
Sharing a vault with another user, even a free user, is a simple matter of sending the vault file and transferring the password using another method, perhaps a message encryption tool. Although it may be highlighted, this tool also has the ability to encrypt individual files and folders and create self-extracting EXEs from them.
Each time Everykey broadcasts an encrypted Bluetooth Low Energy message, it is different from the previous message to prevent a hacker from intercepting the message and sending it again. Since each message is encrypted, there is no way to find a single message from a previous message.
Military-grade encryption traditionally uses a key size equal to or greater than 128 bits. The US government specifies that AES-128 is used for classified (unlisted) information and AES-256 for classified (listed) information. If a business processes information at both levels, it usually uses AES-256 as its standard.
 Source: cdn.trendhunterstatic.com
Source: cdn.trendhunterstatic.com
Two Main Approaches
You want to protect your files and folders by using an encryption process and securely deleting the original. You don't want to be confused by a lot of other features. And you're happy with the cheap one-time fee for a perpetual license.
Folder Lock can encrypt files or simply lock them so that no one can access them. It also offers encrypted lockers for safe storage. Its many other features include file processing, partitioning of free space, secure online backup and self-writing of files.
If you want to share a file with someone and your encryption tool doesn't support PKI, there are other sharing options. Many products allow you to create an executable that deletes itself. You may also find that the recipient can only use a free tool for decryption.
Our software has been tested by RSM (formerly known as SecureState), a US-based security research company. We passed two security tests with the best possible score. This result puts Allkey in the top ~5% of all companies, including some of the biggest brands.
Encryption Algorithms
Another product simply scans files and folders, making their encrypted versions inaccessible. One creates a virtual disk drive that, when enabled, acts like any other drive on your system. When you lock a physical drive, any files you put on it will be completely inaccessible.
BitLocker encryption built into Windows uses AES-128 by default, but can be configured to use AES-256. It's not "military grade" by default, but AES-128 should still be highly secure and resistant to attacks - and it can be military.
 Source: images.squarespace-cdn.com
Source: images.squarespace-cdn.com
Cryptomator allows you to access your files on multiple devices. It is easy to use and compatible with Android, Windows, macOS, iOS and Linux. Mobile apps offer more features than desktop apps. They integrate directly with Google Drive, Dropbox, OneDrive, and WebDAV-based cloud storage services.
When the IBM PC was new, I served as president of the San Francisco Computer Users Group for three years. That's how I met the editorial team at PCMag, who brought me on board in 1986.
Spoof Prevention
In the years since that fateful encounter, I've become PCMag's expert on security, privacy, and identity protection, testing antivirus tools, security suites, and all manner of security software. Editing encrypted files with other tools can be difficult and often requires decrypting the file, making changes, and re-encrypting it.
AxCrypt makes this process seamless, automatically encrypting the file when you open it and re-encrypting it when you close it. It even includes secure storage for your passwords, though it won't capture and replay them like a full-fledged password manager.
When creating and saving a new account, AxCrypt can help with a free random password generator. When the IBM PC was new, I served as president of the San Francisco Computer Users Group for three years.
That's how I met the editorial team at PCMag, who brought me on board in 1986. In the years since that fateful encounter, I've become PCMag's expert on security, privacy, and identity protection, testing antivirus tools, security suites, and all manner of security software.
 Source: api.army.mil
Source: api.army.mil
Who It’s For
Note that the apps listed here focus on protecting local copies of your important files. If your needs include sharing secrets with others, you may want to consider using an email encryption tool instead of or in addition to a local encryption utility.
However, there is a chance that hackers or fraudsters can create a file called 7-zip that contains spyware, malware, ransomware or viruses to compromise your data. To avoid this, download the software from its official website.
You can also use a VPN or anti-malware software and 7-Zip for maximum protection. This very concept of encryption raises a lot of questions for someone who has never had much experience with cyber security. Naturally, when you hear the term "military grade encryption" it becomes even more confusing.
However, if you are familiar with encrypted services, you may have heard the term a lot, especially in relation to various VPN services. For our customer Western Digital Corporation, we developed a data protection feature for the iXpand charger.
Security Audited
A unique device that wirelessly charges both mobile phones while creating an encrypted backup of photos, files and documents on the device. The browser does not offer real encryption and you are completely anonymous. This is because Tor encrypts data using nodes;
when the data traffic leaves the endpoint and reaches its destination, the information is not encrypted. Your data and IP address are visible to anyone monitoring your network and can easily see you. Additionally, Tor has previously been breached by the FBI and attackers have launched SSL attacks on the Tor network.
 Source: thewildfirevpn.com
Source: thewildfirevpn.com
But with a reliable VPN and Tor browser, you can solve all these problems. AES-256 differs from AES-128 and AES-192 by a larger key. This means more computing power is used for encryption and decryption, but all that extra work should make AES-256 harder to crack.
The name Folder Lock suggests that this product simply locks folders behind an encryption system, but nothing could be further from the truth. Folder Lock has the ability to encrypt files and folders and can "lock" them without encryption (that is, hide them from all other programs).
One Of Our Success Stories
However, it can also create encrypted vaults, storage containers that look and function like a regular folder when opened, but are completely inaccessible when locked. For extra money, you can set up secure backup and sync.
Many personal encryption products work by creating a secure container, often called a vault or vault, for sensitive files. This is how Steganos Safe works, but it brings extraordinary flexibility to safe creation. You can, of course, create local vaults, but you can also simply put a mobile vault on a USB drive.
There is a secure cloud option that supports Dropbox, Google Drive and Microsoft OneDrive. You can even wipe an entire disk partition and secure it. With the same form factor and size as the widely distributed TACLANE-Micro, the next-generation NSA Certified TACLANE-FLEX offers improved security features and higher throughput (200 Mbps to 2 Gbps aggregate) to lower the total cost of ownership.
According to NIST, no one can be sure how long AES or any other cryptographic algorithm will remain secure. However, NIST's data encryption standard (known as DES) was the US government standard for nearly 20 years until it was cracked.
 Source: ciphertex.com
Source: ciphertex.com
Why We Picked It
AES supports larger file sizes than DES. Preventing any AES attack quickly is quite tiring, and even with future technological advances, AES has the ability to remain secure for over 20 years. With malware and ransomware attacks on the rise, our data is always at risk of falling into the wrong hands.
The recent Kaseya ransomware attack is a good example of the importance of data protection. It's still important for individuals and businesses to keep information safe with free encryption software. It should come as no surprise that many governments have regulated cryptography - especially its export.
By 1992, cryptography was on the US weapons list. "As auxiliary military equipment." You can create and own encryption technology in the US, but you cannot export it. The Netscape web browser used to have two different versions: a US domestic version with 128-bit encryption and an "international" version with 40-bit encryption (the maximum allowed).
You can even share files and folders with other Cryptomator users to provide access to your vault. Remember that two people cannot open the safe at the same time. It also prevents any malicious actors from accessing your files.
Military Grade Security
But sharing files with people who don't use Cryptomator is impossible. Whether you're logging into your online bank, using a virtual private network (VPN), encrypting files on your hard drive, or storing your passwords in a safe place, you obviously want strong encryption that's hard to crack.
In addition, free VPNs cannot encrypt user data and lack basic security and privacy features such as a kill switch or DNS leak protection. As a result, users suffer from frequent data leakage. As the name Cryptainer suggests, Cypherix Cryptainer PE creates encrypted containers for your files.
You pay a one-time fee for a perpetual license. If you can live with limited technical support and a 100MB size limit for your encrypted vaults, you can use them for free. There is an option to put the mobile app and encrypted vault on a USB drive for complete portability.
With this system, you can create a digital signature that proves that your document is from you and has not been tampered with. How? Just encrypt it with your private key. The fact that your public key is encrypted is all the proof you need.
How Long Will The Aes Last?
PKI support is much less common than support for traditional symmetric algorithms. NordLocker encryption tool comes from the creators of NordVPN, the Editor's Choice virtual private network. You use it to create lockers, encrypted storage containers that give full access to files when opened, but make them completely inaccessible when locked.
NordLocker requires registration, but at $1 a month, it's definitely cheap. You can even use it for free if you don't need more than 2GB of encrypted files.
military grade encryption software, military grade encryption, free data encryption software, free file encryption, military encryption devices, military grade computer security, military grade encryption phone, windows encryption software

 Source: pbs.twimg.com
Source: pbs.twimg.com Source: api.army.mil
Source: api.army.mil Source: news.otc.edu
Source: news.otc.edu Source: i.ytimg.com
Source: i.ytimg.com Source: www.idf.il
Source: www.idf.il
 Source: allindiaroundup.com
Source: allindiaroundup.com Source: res.cloudinary.com
Source: res.cloudinary.com Source: api.army.mil
Source: api.army.mil Source: www.unsw.adfa.edu.au
Source: www.unsw.adfa.edu.au
 Source: discovermilitary.com
Source: discovermilitary.com Source: c8.alamy.com
Source: c8.alamy.com Source: media.defense.gov
Source: media.defense.gov Source: api.army.mil
Source: api.army.mil Source: media.defense.gov
Source: media.defense.gov
 Source: images.template.net
Source: images.template.net Source: image.slidesharecdn.com
Source: image.slidesharecdn.com Source: mailbakery.s3.amazonaws.com
Source: mailbakery.s3.amazonaws.com Source: static.vecteezy.com
Source: static.vecteezy.com Source: assets-global.website-files.com
Source: assets-global.website-files.com
 Source: media.defense.gov
Source: media.defense.gov Source: 1.bp.blogspot.com
Source: 1.bp.blogspot.com Source: pbs.twimg.com
Source: pbs.twimg.com Source: www.boeing.com.au
Source: www.boeing.com.au Source: media.defense.gov
Source: media.defense.gov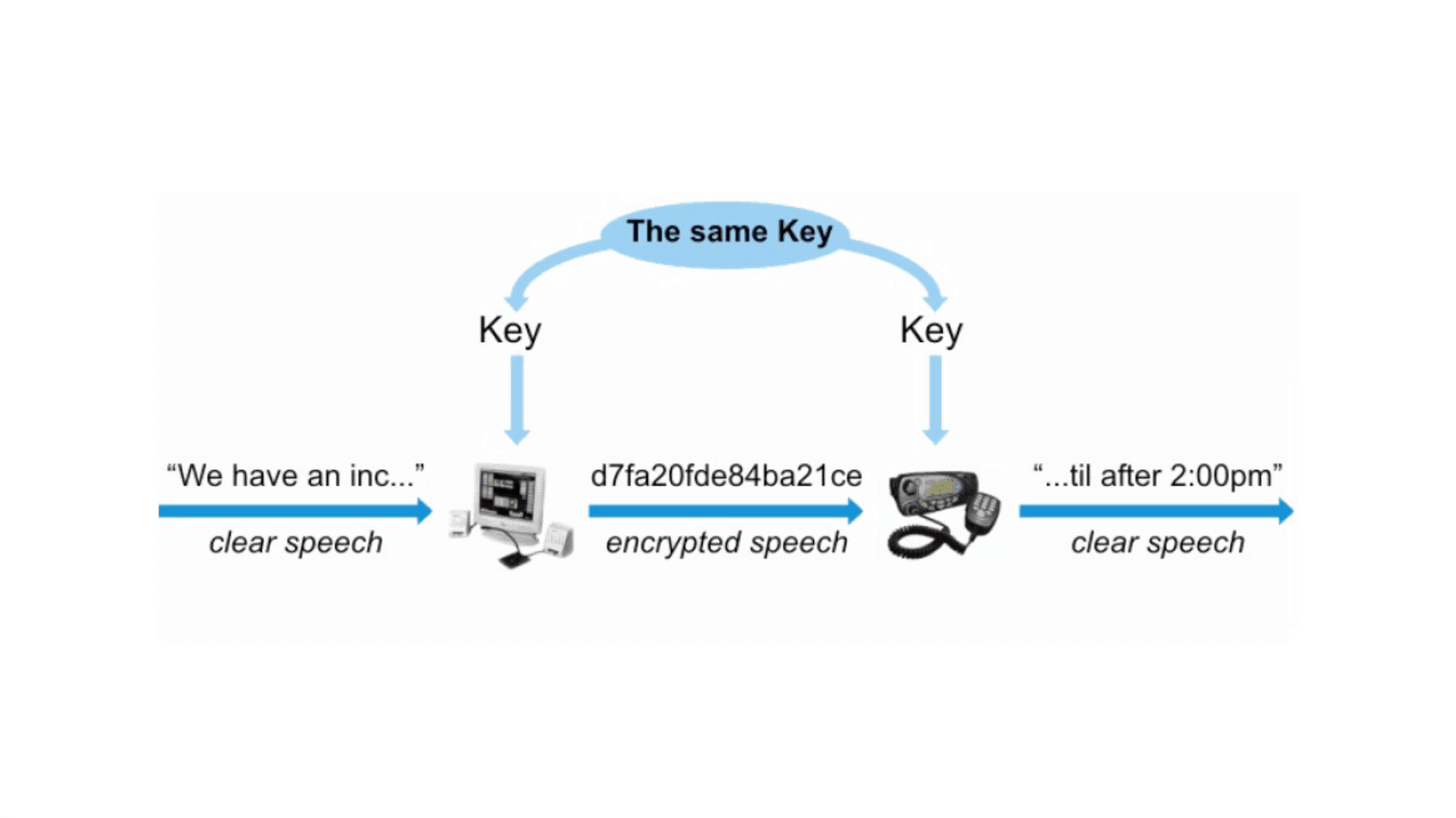
 Source: cdn.trendhunterstatic.com
Source: cdn.trendhunterstatic.com Source: i.pinimg.com
Source: i.pinimg.com Source: mediaboxent.com
Source: mediaboxent.com Source: cryptome.org
Source: cryptome.org Source: thumbs.dreamstime.com
Source: thumbs.dreamstime.com