Military Encryption Devices - PD COMSEC Layer 3 Filler Project Manager Aaron Clayton said the NGLD-Small devices are certified by the National Security Agency (NSA) to process and store electronic keys classified as "top secret." Stan Scofield, PD COMSEC Special Projects Specialist, Program Executive Office, Command, Control, Communications and Tactics (PEO C3T), said, “Instructors came to us with various devices and taught Soldiers how to use them.
it didn't take long to get them up and running on new devices." The TACLANE Ransomware Operator Training Course is a four-day course offered at our facilities in Scottsdale, Arizona and Annapolis Junction, Maryland. The course combines classroom presentations and hands-on exercises to teach you
Military Encryption Devices
 Source: www.taitradioacademy.com
Source: www.taitradioacademy.com
how to install, configure and maintain TACLANE-FLEX (KG-175F), TACLANE-Nano (KG-175N), TACLANE-Micro (KG-175D), TACLANE-1G Encryptors (KG-175G) and TACLANE-10G (KG- 175X) in practical use. The course also includes a complete training module on our encryption management software GEM® One. Students who pass a short written and practical exam at the end of the course receive a certificate. We use cookies to improve your experience on the website.
Taclane Encryptor Training
site, you agree to our use of cookies Learn more The TACLANE Trusted Sensor Training Software course is a one-day course offered at our facilities in Annapolis Junction, Maryland and Scottsdale, Arizona. the hands-on course provides the in-depth knowledge and training required to activate, configure and maintain TACLANE Trusted Sensor software for network intrusion detection and mitigation.
Topics covered include cybersecurity principles, policy creation, alert configuration, and modes of operation. Students who pass a short written and practical exam at the end of the course receive a certificate. HYPE v4.2.5 IPMEIR v1.0 HYPE VLAN ACC & KMI OTNK Sharing the same form factor and fit as the ubiquitous TACLANE-Micro, the next-generation NSA-certified TACLANE-FLEX provides advanced security features and scalable bandwidth (from 200 Mbps unit up to 2 Gbps)
 Source: cdn.trendhunterstatic.com
Source: cdn.trendhunterstatic.com
to reduce the total cost of ownership. The devices were also tested during a Network Integration Evaluation (NIE) exercise at Fort Bliss, Texas, and White Sands Missile Range, New Mexico, USA, to verify their ability to meet the military's stringent environmental requirements.
You're never alone when you partner with General Dynamics to protect critical information. With the world's largest NSA-certified ransomware deployment base, General Dynamics is committed to supporting our customers worldwide with 24/7 technical support. If encryption keys are stored centrally in one place, this can lead to a single point of failure.
Taclane Trusted Sensor Software Training
This is exactly what happens with many insider hacks, which account for over 20% of hacks. An attacker or malicious insider tries to gain access to the administrator account, after which all secrets are lost. The best way to protect against internal hacking is to implement a fully distributed key management system to avoid a single point of failure.
Networks today carry more traffic, are connected to more devices, and are under more attack than ever. In response to these evolving cybersecurity threats, General Dynamics developed the TACLANE®-1G (KG-175G). The TACLONE-1G is a compact, more energy-efficient, high-speed 1Gbps network encryptor with Cyber-Defense support.
 Source: i.pinimg.com
Source: i.pinimg.com
The TACLONE-1G is robust for both tactical and strategic environments and is NSA certified for Top Secret SCI and lower information security. TACLANE-1G supports Agile VLAN and can work with TACLANE Trusted Sensor software to improve network discovery capabilities.
The MCA is a compact and versatile cryptographic device specifically designed to secure airborne radio communications up to NATO security level and half the size of the legacy KY100. MCA can also be used on the ground and on ships to provide ground/ground-to-air radio communications.
/ Customer Support
General Dynamics offers a variety of product training courses at our Annapolis Junction, Maryland and Scottsdale, Arizona facilities. The courses combine classroom presentations and hands-on exercises designed to educate users on how to install, configure, maintain and use the latest security products in a practical work environment.
Students who pass a short written and practical exam at the end of the course receive a certificate. The most commonly used symmetric encryption algorithm is Advanced Encryption Standard, or better known as AES. AES is a block encryption algorithm, which means it handles encryption in blocks - the most commonly used block sizes are 128-bit and 256-bit.
 Source: mediaboxent.com
Source: mediaboxent.com
"Military-grade" encryption means 256-bit AES encryption, while most financial institutions have adopted 128-bit AES encryption. It is important for users to ensure that their TACLANE-based security solutions are integrated and used with approved support equipment to meet mission requirements.
Using accessories tested and approved by General Dynamics for use with TACLANE devices reduces risks associated with interoperability, redundancy, environmental factors and even warranty coverage. For a complete list of tested and approved accessories available for purchase and supported by General Dynamics, see the TACLANE Approved Product List (APL).
To Secure Radio Communications At Nato Secret Level
If you need a product that is not on the list, contact us. Finally, the confidentiality of the exchange is the most important aspect of data protection. This is the weakest link in security. Attackers often look for flaws in secret exchanges to gain access to protected data.
This includes relaxing Transport Layer Security (TLS), which is commonly used in the HTTPS protocol. The best way to implement a secret exchange protocol should have three key features: (1) immunity to man-in-the-middle attacks, (2) complete secrecy of transmission, and (3) zero knowledge.
 Source: cryptome.org
Source: cryptome.org
Doing all three is hard, very hard, but a service provider that can do all three is safer than one that can't. The General Dynamics High Assurance Encryption product family is widely used today to protect national security systems, information and networks from persistent threats and protect our assets in cyberspace on land, air, sea and space.
From embedded systems to tactical enterprise peripherals, these NSA Type 1 certified products protect sensitive information with the highest level of security, defending against dynamic threats and protecting the nation's most sensitive information. In my opinion, 128-bit AES with an appropriate encryption mode (like GCM or CBC) is better than 256-bit AES with a lower encryption mode (like ECB).
Which Taclane Is Right For Your Mission?
ECB mode detects a repeating data pattern. Although the block size is larger, an attacker can use statistical analysis to guess the secret. The details of how each mode works are beyond the scope of this blog.
TACLANE, the world's most widespread family of Type 1 certified encryption, has been protecting critical information and securing national security systems for more than 20 years. Building on this legacy, the TACLAIN portfolio continues to modernize and enhance technologies to protect against today's advanced threats and secure tomorrow.
 Source: thumbs.dreamstime.com
Source: thumbs.dreamstime.com
We use cookies to improve your experience on the website. By continuing to visit this page, you agree to our use of cookies. Learn more You're never alone when you partner with General Dynamics to protect critical information.
With the world's largest NSA-certified ransomware deployment base, General Dynamics is committed to supporting our customers worldwide with 24/7 technical support. Certified for security Top Secret/SCI and below, TACLANE's portfolio includes both secure Small Format Embedded Network Encryptors (INE) and high performance encryption platforms (total throughput from 200Mbps to 20Gbps).
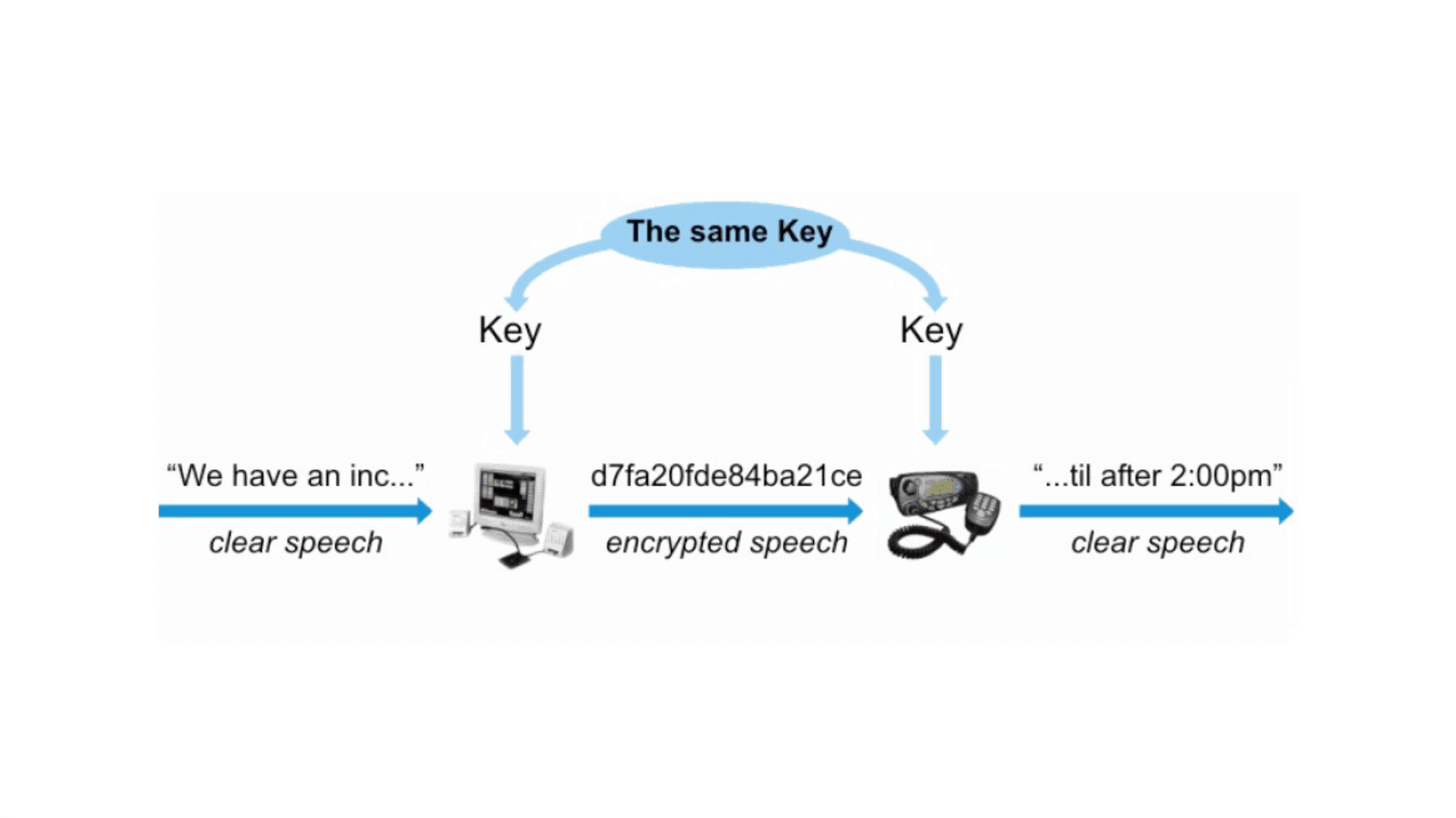
/with). Compare our TACLANE network encoders and decide which one is best for your application. There are two main classes of encryption: (1) symmetric encryption and (2) asymmetric encryption. Simply put, symmetric encryption means that the same key is used for both encryption and decryption.
Asymmetric encryption means that the keys used for encryption and decryption are different. For "military grade" encryption, let's just focus on symmetric encryption. Based on the above, no attacker will waste time and resources cracking even a 128-bit AES key.
Therefore, the myth of using "military" encryption is quite meaningless, 128-bit AES is more than enough for the next 10 years, even with improvements in the performance of computers and supercomputers. How secure is 128-bit AES?
If you have access to one of the world's fastest supercomputers, it can process 33.86 PentaFLOPs (10¹⁵) per second. Let's say it takes 1000 FLOPs (floating point operations) to check if you broke the key. Using brute force (ie try all combinations) to crack a 128-bit key (equivalent to 3.4 x 10³⁸ combinations) takes approximately 318 billion billion years on the world's fastest computer.
The solar system is only 4.6 billion years old. A 256-bit key has 1.1 x 10⁷⁷ combinations. You can calculate how many years it would take for the world's fastest supercomputer to be hacked.
military grade encryption phone, general dynamics encryption devices, military grade encryption software, military grade encryption vpn, military encryption software, dod encryption standard, military grade encryption, encryption decryption device army